CBCTF 2024 Part 2
This is part 2 to my CTF writeup for CBCTF 2024.
In this writeup, I’ll be discussing the following challenges from the Qualifying’s Packet Analysis category:
Code Hunter [50 pts]
Description: Hunt it
This was an easy point, you are given a pcap file and you are asked to find the flag. I opened the pcap file in Wireshark and searched for the flag format CBCTF{ and found the flag in a HTTP request of a webpage!
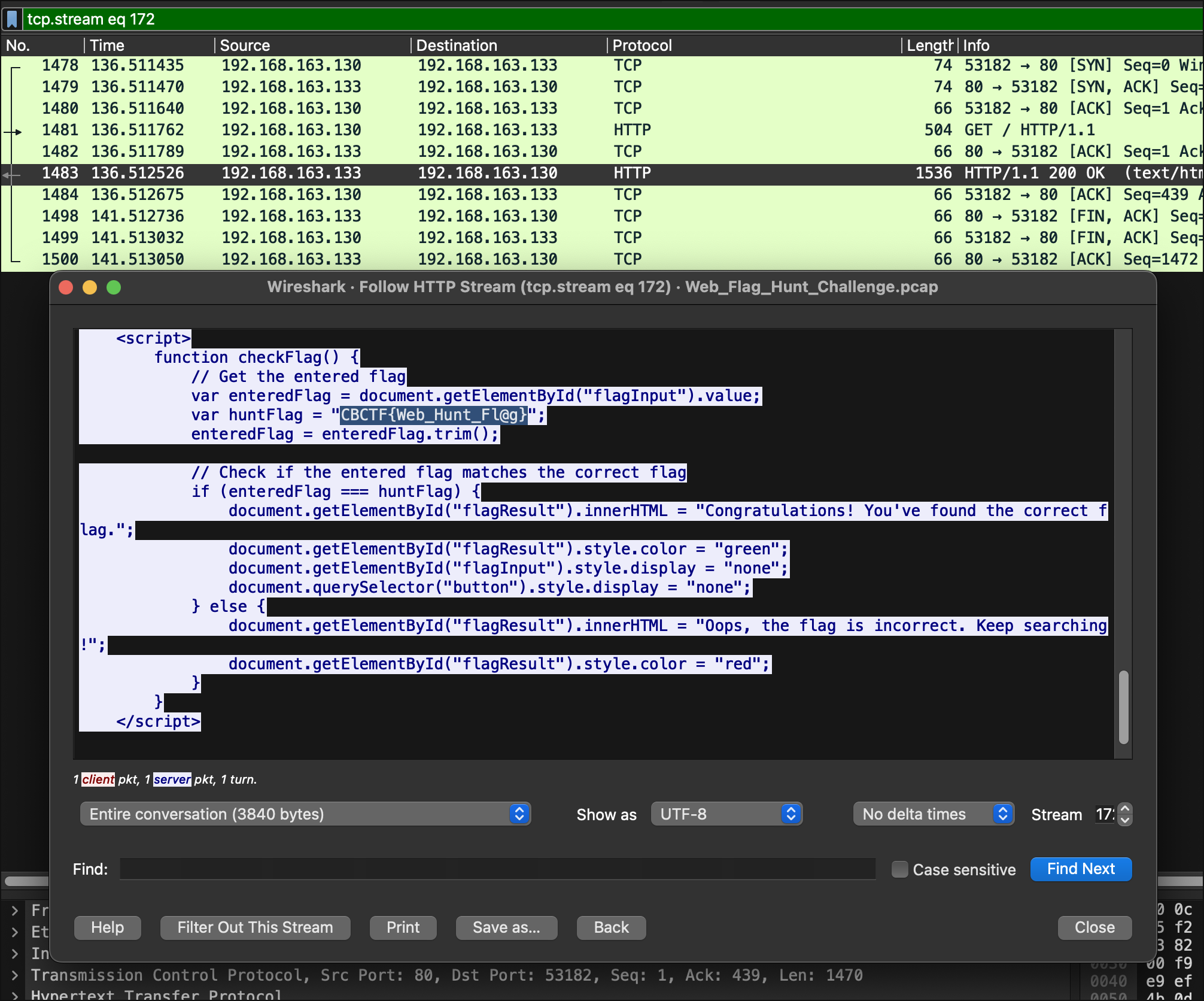
Flag:
CBCTF{Web_Hunt_Fl@g}
Neddih ASR challenge [150 pts]
Description: Mirror Image
For this challenge, you are given a pcap file and the obvious hint here is ASR == RSA in reverse and Neddih == hidden. Upon opening the pcap file in Wireshark, I navigated to export objects and found a PNG file named C.png. Extracted that and it’s a image of the C = .
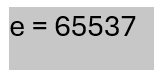
As you know in RSA you need some parameters to decrypt the ciphertext. So, I analyzed the image and saw the file size was a little to big for a PNG file. With that info, I tried carving the file using binwalk and found E.png. This is the exponent used in RSA.
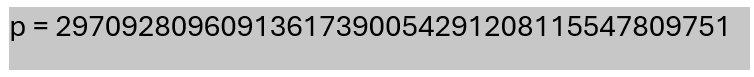
Now, I just continue the same method on the E.png file and found p.png and q.png. These are the prime numbers used in RSA. With these, I can decrypt the ciphertext using RsaCtfTool.
Images below:
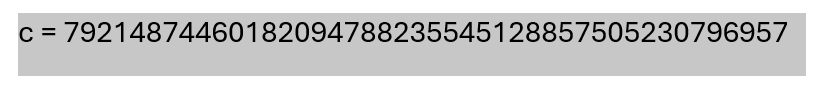

C = 79214874460182094788235545128857505230796957
E = 65537
p = 29709280960913617390054291208115547809751
q = 2677
RsaCtfTool git:(master) python3 RsaCtfTool.py -e 65537 -p 29709280960913617390054291208115547809751 -q 2677 --decrypt 79214874460182094788235545128857505230796957
private argument is not set, the private key will not be displayed, even if recovered.
['/var/folders/10/kmsfxftj7s1fp60x57jff_q80000gn/T/tmprbswm_29']
Results for /var/folders/10/kmsfxftj7s1fp60x57jff_q80000gn/T/tmprbswm_29:
Decrypted data :
HEX : 0x000043424354467b37337235334e38554e317d
INT (big endian) : 22886997224620714805923237942802445644157
INT (little endian) : 2791888307128338328899737028283428778367188992
utf-8 : CBCTF{73r53N8UN1}
STR : b'\x00\x00CBCTF{73r53N8UN1}'
Flag:
CBCTF{73r53N8UN1}
There you have it, the writeup for the Packet Analysis category in CBCTF 2024 Qualifiers. There is actually another one, but I’ll leave that for another writeup as that is takes a lot more steps and has a bit of OSINT involved. Stay tuned!